The man suspected of participating in a large DDoS attack on an antispam organization that caused intermittent Internet hiccups drove around Spain in a van he used as a mobile office, Spain's Interior Ministry said Sunday.
The van was equipped with "various antennas" that were used to scan frequencies, the ministry said in a news release. On Thursday, Spanish police arrested a 35-year-old Dutch man in Barcelona suspected of conducting cyberattacks against Spamhaus, a nonprofit group that develops widely used lists of networks identified as sending spam.
Spanish police published a video of a sparse residence they raided. Images showed the room was strewn with wires and computer equipment, including routers, a Mac Mini computer, laptops, an antennae and a single cot with the book "Quicksilver" by Neal Stephenson on it. Also shown were several rubber stamps, two of which were emblazoned "NATO secret" and "NATO unclassified."
The man has been identified by an official close to the investigation as Sven Kamphuis, who has denied involvement. Dutch authorities only identified the suspect by the initials "S.K." for privacy reasons. Kamphuis has said he believes the attacks originated with members of Stophaus, a group aiming to shutdown Spamhaus for its antispam work.
The DDoS attack was estimated to peak at more than 300Gbps, making it one of the largest attacks on record, but computer security experts disagreed somewhat over its broader effect on the Internet. The attack caused problems for some European Internet exchanges nodes, or places where ISPs link to transfer traffic to one another.
The Interior Ministry, which did not name the suspect, said they seized two laptops and documents from the residence. At the time of his arrest, the man, from Alkmaar, Netherlands, claimed to be the minister of telecommunications and foreign affairs of the Republic of CyberBunker, Spanish police said.
CyberBunker.com is a hosting provider based in a former military facility in the Netherlands. It specializes in so-called "bulletproof" hosting, or one that resists law enforcement efforts to remove certain content from the Internet. It claims it has no involvement in spam and does not allow SMTP traffic, the protocol used to send email.
Kamphuis runs a network provider called CB3ROB, which provided services for CyberBunker. CB3ROB had been blacklisted by Spamhaus for activity related to spamming botnets and extortion scams.
Send news tips and comments to jeremy_kirk@idg.com. Follow me on Twitter: @jeremy_kirk



 The Radeon HD 7990 has a massive heatsink that runs the entire length of the card. Three amazingly quiet fans keep everything cool.
The Radeon HD 7990 has a massive heatsink that runs the entire length of the card. Three amazingly quiet fans keep everything cool.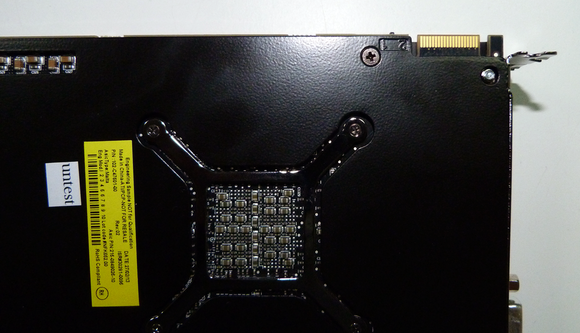 See that edge connector near the card's mounting bracket? That will enable you to build a quad-GPU monster system by running two of these cards in CrossFire mode.
See that edge connector near the card's mounting bracket? That will enable you to build a quad-GPU monster system by running two of these cards in CrossFire mode.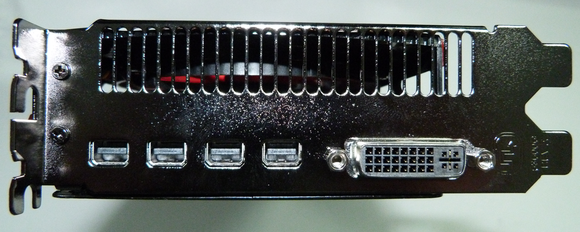 Four Mini DisplayPort connections, one DVI port, and AMD's Eyefinity technology deliver plenty of multi-monitor options.
Four Mini DisplayPort connections, one DVI port, and AMD's Eyefinity technology deliver plenty of multi-monitor options. Should you decide to add a Radeon HD 7990 to your rig, make sure it'll fit: The board measures a full 12 inches long.
Should you decide to add a Radeon HD 7990 to your rig, make sure it'll fit: The board measures a full 12 inches long. Origin PCOrigin PC will offer Radeon HD 7990 cards across its entire desktop line starting immediately.
Origin PCOrigin PC will offer Radeon HD 7990 cards across its entire desktop line starting immediately.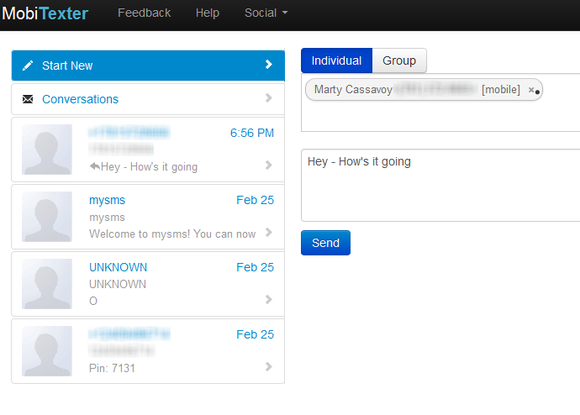 MobiTexter's Web app is clean and uncluttered, as a text app should be.
MobiTexter's Web app is clean and uncluttered, as a text app should be. Surface Pro was hot when it launched, but overall sales are disappointing.
Surface Pro was hot when it launched, but overall sales are disappointing. IDC says PC sales dropped 14 percent in the most recent quarter.
IDC says PC sales dropped 14 percent in the most recent quarter.