Dell described a bleak outlook for the PC industry on Good Friday in a document filed with the U.S. Securities and Exchange Commission.
The document, one of several filed by the company in connection with its move to go private, includes a laundry list of ills that pretty much defines life for computer makers in the post PC era.
That list identifies factors contributing not only to Dell's present and future performance, but paints a picture of the uncertain world ahead for all PC makers.
Dell's pitch
In its filing, Dell makes it sound like it would do present stockholders a favor by buying out their stock and taking the company off the stock market. By scooping up all Dell common shares in the market, it noted, stockholders will "no longer be exposed to the various risks and uncertainties related to continued ownership of Common Stock."
Among those uncertainties are decreasing revenues from Dell's bread and butter products—desktop and laptop PCs. The company acknowledges it has no no idea when or if this trend will end.
 IDGNSMichael Dell, founder and CEO
IDGNSMichael Dell, founder and CEO Factors cited by Dell as contributing to present revenue declines include "uncertain adoption" of Windows 8, slowdowns of Windows 7 upgrades in the enterprise, longer PC replacement cycles, and, of course, substitution of tablets and smartphones for PCs.
Not only are Windows sales lagging, but Dell reported that alternative operating systems are gaining traction in the market, a trend hurting the company's PC offerings, which primarily run Windows.
Making matters worse, when someone finally upgrades a PC, the margins for the company on that sale won't be very high due to commoditization of pricing for PCs.
Those revenue declines might be offset by sales of smartphones and tablets but, alas, the company confesses it has "very little presence" in those markets.
In the past, Dell has been able to rake in revenues from high-margin PC products, but that market, like the rest of the PC market, is in decline. Dollars for PCs are moving to lower-margin products, Dell noted, "a segment in which the company has historically been much less competitive."
Dell is also being hurt by the "Bring Your Own Device" trend in the workplace, it said, because that trend favors products produced by the company's competitors which "have greater appeal to consumers than [Dell's] current products."
Dell's founder and CEO Michael Dell announced he wanted to take the company private in February and put a $2 billion deal on the table to do it. However, he left the door open for Dell's board of directors to receive offers from other interested parties. Earlier this week, those offers came in.
Battling buyout offers
A group affiliated with a private equity fund managed by Blackstone and another group led by Carl Icahn both submitted buyout offers to the board's committee reviewing such offers.
Blackstone's deal includes a per share offer of $14.25; Icahn's, $15 a share. CEO and Chairman Dell's offer is $13.65 a share. All the offers would provide stockholders with a tidy profit, based on $10.88 per share price at which Dell stock was selling when news broke of a proposal to take the company private.
In high finance circles, the devil in deals like this is in the details, which is why the committee noted:
"The Special Committee has not determined that either the Blackstone proposal or the Icahn proposal in fact constitutes a superior proposal under the existing merger agreement and neither is at this stage sufficiently detailed or definitive for such a determination to be appropriate. There can be no assurance that either proposal will ultimately lead to a superior proposal."
"While negotiations continue the Special Committee has not changed its recommendation with respect to, and continues to support, the company's pending sale to entities controlled by Michael Dell and Silver Lake Partners," it added.
The committee said that CEO Dell is willing to "explore in good faith the possibility of working with third parties regarding alternative acquisition proposals"—a wise move, since, if Blackstone or Icahn acquired the company, its founder could find himself without a job.
However, since there's no timetable for ironing out what to do about the deals now on the table, Dell will likely helm his company for some time to come.
Microsoft joins in
In addition to Silver Lake, Microsoft has also thrown in with Founder Dell for the tune of $2 billion. That's led to all kinds of speculation about Redmond's intentions.
It's well known that Microsoft hasn't been totally satisfied with the quality of the hardware being produced for its software. That dissatisfaction led Redmond to produce its own Windows-based Surface line of tablets.
By buying a piece of Dell, Microsoft might be buying a bigger say over what kind of hardware is produced for its software, some Microsoft watchers have speculated. It could also mean that Microsoft is contemplating an exit from the tablet business somewhere down the road.
If CEO Dell can take his company private, he believes he will have greater freedom to take it where it needs to go if it's to survive in the post-PC era. That path includes the continued production of PCs, but with a heavy focus on the enterprise market.
However, Dell's investors believe he's low-balling them with his offer, which means the company is in for some interesting times as its board tries to reconcile the interests of everyone involved.

 IDGNSMichael Dell, founder and CEO
IDGNSMichael Dell, founder and CEO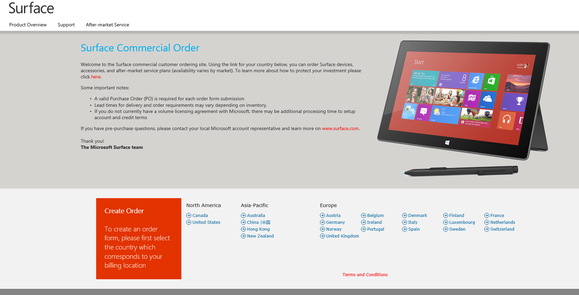 Microsoft's website for commercial Surface tablet orders.
Microsoft's website for commercial Surface tablet orders.
 IntelIntel processor
IntelIntel processor
 The session mux lets you see and edit the super flexible audio signal routing.
The session mux lets you see and edit the super flexible audio signal routing. Looks can be deceiving in MuLab. Right-click any object and you'll usually find the functionality you need.
Looks can be deceiving in MuLab. Right-click any object and you'll usually find the functionality you need.
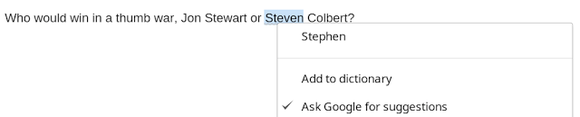 GoogleThe "Ask Google for suggestions" feature is now available to Windows, Linux, and Chrome OS users.
GoogleThe "Ask Google for suggestions" feature is now available to Windows, Linux, and Chrome OS users.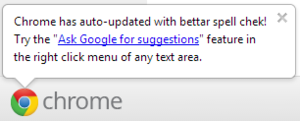

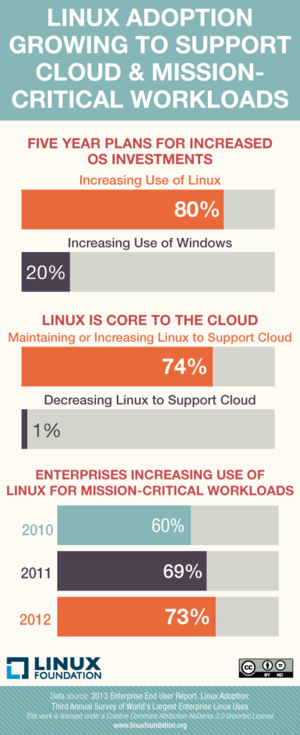 The Linux FoundationLinux continues to gain hold in enterprises (Click image to enlarge.)
The Linux FoundationLinux continues to gain hold in enterprises (Click image to enlarge.) Creative Assembly Creative Assembly is using Intel's new DirectX extensions in developing its game Total War: Rome II.
Creative Assembly Creative Assembly is using Intel's new DirectX extensions in developing its game Total War: Rome II. AMDLittle is known about AMD's Radeon HD 7990, other than it will have two 7900-series GPUs and three cooling fans.
AMDLittle is known about AMD's Radeon HD 7990, other than it will have two 7900-series GPUs and three cooling fans. AMDThe AMD Radeon Sky series videocards are designed to power servers for cloud gaming.
AMDThe AMD Radeon Sky series videocards are designed to power servers for cloud gaming. Sticky Password's folders help keep things organized, but the excellent browser integration means you rarely need to manually find things.
Sticky Password's folders help keep things organized, but the excellent browser integration means you rarely need to manually find things.
 Fadi Chehade, ICANN CEO
Fadi Chehade, ICANN CEO
 Having complex PC games like Civilization 5 at your fingertips is amazing.
Having complex PC games like Civilization 5 at your fingertips is amazing. Snap the Edge into it's gamepad chassis accessory and you have a viable handheld gaming platform, but it's hard to use anywhere besides your couch.
Snap the Edge into it's gamepad chassis accessory and you have a viable handheld gaming platform, but it's hard to use anywhere besides your couch. The Edge has a serviceable display, but it's not very vibrant and can't handle 1080p video.
The Edge has a serviceable display, but it's not very vibrant and can't handle 1080p video.