Two privacy-focused email providers have launched the Dark Mail Alliance, a project to engineer an email system with robust defenses against spying.
Silent Circle and Lavabit abruptly halted their encrypted email services in August, saying they could no longer guarantee email would remain private after court actions against Lavabit, reportedly an email provider for NSA leaker Edward Snowden.
Their idea, presented at the Inbox Love email conference in Mountain View on Wednesday, is for an open system that could be widely implemented and which offers much stronger security and privacy. As envisioned, Dark Mail would shield both the content of an email and its "metadata," including "to" and "from" data, IP addresses and headers. The email providers hope a version will be ready by next year.
"The issue we are trying to deal with is that email was created 40 years ago," Jon Callas, CTO and founder of Silent Circle, in a phone interview. "It wasn't created to handle any of the security problems we have today."
Silent Circle, Lavabit and at least one VPN provider, CryptoSeal, shut down their services fearing a court order forcing the turnover of a private SSL (Secure Sockets Layer) key, which could be used to decrypt communications.
Lavabit was held in contempt of court for resisting an order to turn over its SSL key, which in theory allowed the government to decrypt not only Snowden's communications but also those of its 400,000 users. Ladar Levison, Lavabit's founder, is appealing.
Callas said Dark Mail is a collaboration with Levison. Rather than create a closed email service, they decided to design Dark Mail with open-source software components that could be used by any email provider.
"We need 1,000 Lavabits all around the world," he said.
Microsoft's David Dennis, lead principal program manager for the company's Outlook.com webmail portal, said Dark Mail is an "interesting proposal."
"We pay attention to any new innovations, protocols, standards and proposals impacting online communications," Dennis wrote in an email. "And we're always open to discussions with potential partners."
Representatives of Google and Yahoo who attended Inbox Love did not have an immediate comment.
Dark Mail will be crafted around XMPP, a web messaging protocol known by its nickname Jabber, along with another encryption protocol created by Silent Circle called SCIMP (Silent Circle Instant Message Protocol), Callas said.
An adapter will be built that will enable Dark Mail within different email clients. "There's no reason why you couldn't modify Outlook and Exchange to do this," he said.
The private key used to encrypt email will be held on users' systems and not retained by a service provider. Even if the government forced a SSL key to be turned over, users would not be compromised "because all of the messages are encrypted to keys that are sitting in the hands of the recipient," Callas said.
In that case, the party interested in the communication would have to request the encryption key from a person or find another way to decrypt the message.
Snowden's documents showed the NSA was also collecting email metadata, which reveals a sender's and recipient's email addresses, subject line of the email, IP addresses and more. Dark Mail will encrypt the metadata, using the XMPP protocol to signal when a new message has arrived, Callas said.
The alliance is also considering longstanding problems around encryption keys, such as public and private key pairs that are in use for years. "The longer that a key stays around, the bigger of a vulnerability it is," Callas said.
One idea is to create a protocol that would only keep a static public key for just a few hours or a day and then refresh it. Older messages would need to be re-encrypted with a new key to maintain access, but it would provide much better long-term protection for sensitive messages, Callas said.
Also under consideration is "forward secrecy," an encryption feature that limits the amount of data that can be decrypted if a private key is compromised in the future.
Wide use of encrypted email has implications for companies such as Google, which displays advertisements based on email content. In industries such as financial services, companies are required to retain email for compliance regulations.
There's also a convenience factor, as email encryption isn't necessarily easy to implement, especially as people use multiple tablets and mobile phones and desktop computers. Callas said Dark Mail will be flexible, allowing users to send unencrypted email if they don't need an extra level of security.
Send news tips and comments to jeremy_kirk@idg.com. Follow me on Twitter: @jeremy_kirk
 Livescribe 3 smartpen
Livescribe 3 smartpen Remove the rubber cap on one end of the Livescribe 3 smartpen to get to its charging port; that cap also doubles as a capacitive stylus.
Remove the rubber cap on one end of the Livescribe 3 smartpen to get to its charging port; that cap also doubles as a capacitive stylus. An LED indicator gives you an at-a-glance look at the Livescribe 3's status. This blue light means it's connected via Bluetooth to your iOS device.
An LED indicator gives you an at-a-glance look at the Livescribe 3's status. This blue light means it's connected via Bluetooth to your iOS device. Flip over a block of handwritten notes in the Feed view of the Livescribe+ app, and you can convert it into text.
Flip over a block of handwritten notes in the Feed view of the Livescribe+ app, and you can convert it into text. Play back a pencast you've recorded with Livescribe+, and the app highlights the relevant portion of your notes in green as the audio plays.
Play back a pencast you've recorded with Livescribe+, and the app highlights the relevant portion of your notes in green as the audio plays. Livescribe 3 Pro smartpen
Livescribe 3 Pro smartpen

 IDGNSA protester dressed as U.S. President Barack Obama joins the rally against government surveillance programs.
IDGNSA protester dressed as U.S. President Barack Obama joins the rally against government surveillance programs. IDGNSProtesters gather in Washington, D.C., Saturday for a rally opposing mass surveillance by the U.S. National Security Agency.
IDGNSProtesters gather in Washington, D.C., Saturday for a rally opposing mass surveillance by the U.S. National Security Agency.  IDGNSLauren Schreiber, community outreach and event coordinator at the Council on American Islamic Relations in Washington, D.C., holds up a sign during a Saturday protest.
IDGNSLauren Schreiber, community outreach and event coordinator at the Council on American Islamic Relations in Washington, D.C., holds up a sign during a Saturday protest. Image: Geek.com
Image: Geek.com I'm a lemonade mogul. Pure capitalism.
I'm a lemonade mogul. Pure capitalism. Spreadsheets from 2013 still look pretty much like spreadsheets from 1979.
Spreadsheets from 2013 still look pretty much like spreadsheets from 1979. Go home, E.T. Nobody likes you.
Go home, E.T. Nobody likes you.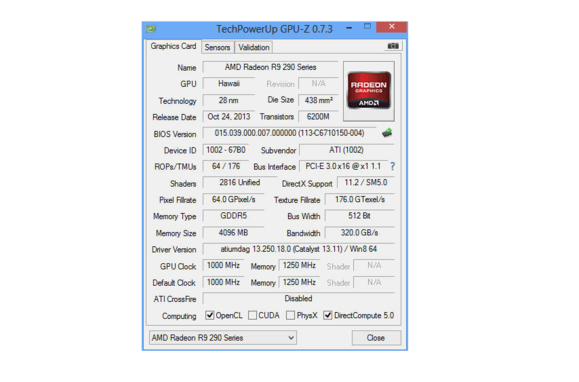 The Radeon R9 290X's full specifications, thanks to GPUz.
The Radeon R9 290X's full specifications, thanks to GPUz.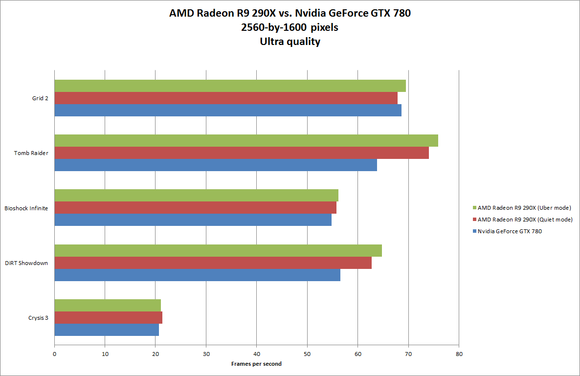 On our game benchmarks, at Ultra settings and a resolution of 2560 by 1600 pixels, the Radeon R9 290X bested the GeForce GTX 780 nearly every time.
On our game benchmarks, at Ultra settings and a resolution of 2560 by 1600 pixels, the Radeon R9 290X bested the GeForce GTX 780 nearly every time.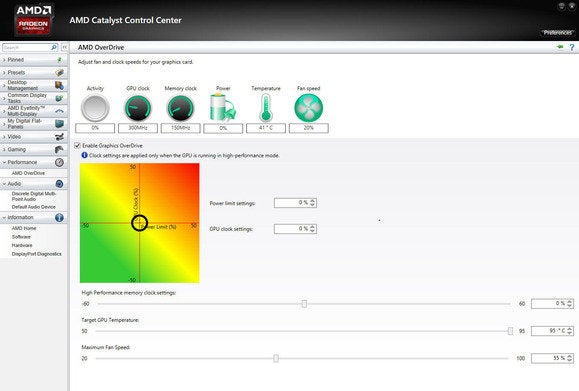 AMD's updated OverDrive option.
AMD's updated OverDrive option.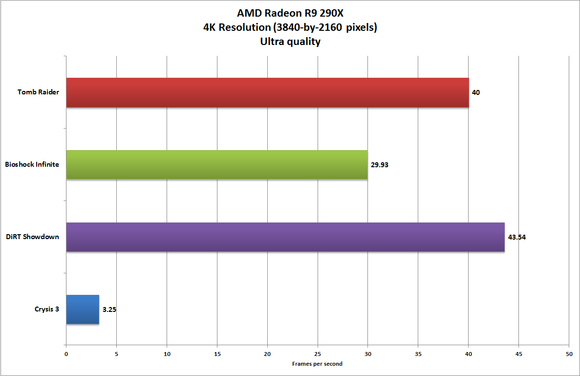 Frame rates for games running at 4K resolution and Ultra settings were surprisingly good.
Frame rates for games running at 4K resolution and Ultra settings were surprisingly good.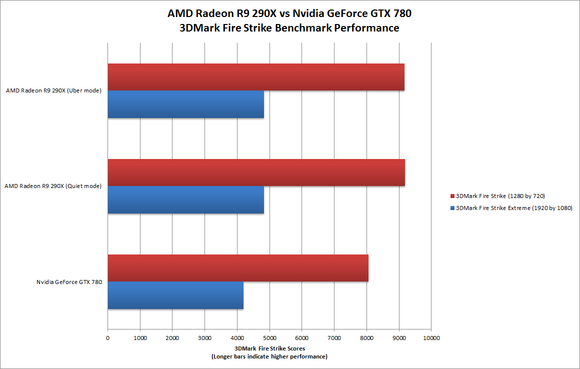 The Radeon R9 290X outperformed the Nvidia GeForce GTX 780 in artificial benchmarks, too.
The Radeon R9 290X outperformed the Nvidia GeForce GTX 780 in artificial benchmarks, too.