"Privacy is dead—get over it," has been a mantra of private investigators for years.
But continuing revelations about how many different ways personal privacy is still disappearing are still enough to unnerve people. It is not just about the trail everybody leaves from the websites they visit, or from security cameras in public places. It is also about smart cars. It is about the cellular towers that serve their smartphones. And it is now also about their friendly brick-and-mortar retailer.
One example of many is clothing retailer Nordstrom, which began tracking shoppers in its stores about a year ago through the Wi-Fi signals from their smartphones.
At least the company was somewhat transparent about it—it posted a sign telling customers what it was doing. But that generated enough complaints for it to end the program in May.
Of course, Nordstrom is not the only retailer looking to track shoppers in its physical stores. And at one level, they and their defenders argue that this is not a big deal—that they aren't doing anything more intrusive than those in the online world who track the activities of shoppers and then try to pitch them ads that will be more "relevant." They're just catching up.
Used to it yet?
They could argue that it is less intrusive than plenty of other data collection, from social networking sites like Facebook to government, in the form of the National Security Agency (NSA). Stillman Bradish, co-founder of The Wireless Registry, a D.C.-based start-up that is reportedly designing ways for consumers to opt out of the tracking, told the Washington Post that, in general, Wi-Fi tracking doesn't collect PII (Personally Identifiable Information).

And, as plenty of privacy experts have pointed out, the "new normal" today is for people to spill every detail of their lives online, including where they shopped and what they bought.
Veteran private investigator Steven Rambam has been telling audiences for years that the logical result of all that voluntary sharing is that, "Privacy is dead, and you guys murdered it."
At one point in a presentation to The Next HOPE (Hackers On Planet Earth) conference three years ago, Rambam asked how many had Facebook pages. Every hand went up. Then he asked those who had read Facebook's Terms of Service to keep their hands up. Every hand went down.
He was even more critical of users of social networks like Swipely, designed for friends to share their purchase history. "Why would you put your shopping history on (things like that)?" he said. "You deserve every bit of screwing that you get."
How they watch you
Still, consumers have a sense—logical or not—that they have some control over the voluntary sharing they do, while they have little or none over a retailer tracking their movements in a store.
The tracking is possible because of the MAC (Media Access Control) address that all Wi-Fi or Bluetooth-enabled devices have—a unique, 12-digit code to help routers send data to the right recipient. When a Wi-Fi card is on, looking for networks to join, it is detectable by local routers, such as those in a retail establishment.
Through that, the company can learn how long people stand in line at a cash register, what aisles they visit and for how long, what promotions are more effective, who visits their stores more than once, what spot in the store draws the most people and much more.

This information is logged and uploaded to third-party companies that conduct data analytics. According to Jules Polonetsky, executive director of the Washington, D.C.-based think tank Future of Privacy Forum (FPF), nine firms have most of the market for analyzing tracking data, but there are 40 or more in the field.
The obvious goal of all this is, on its face, rather benign. "They want to sell you stuff," Rambam said. But privacy advocates say it can and does go well beyond that.
"This tracking is happening generally without people knowing, and it doesn't even leave cookies or make connections that you can monitor," said Parker Higgins, an activist with the Electronic Frontier Foundation (EFF).
"It also ignores that different norms govern what's reasonable in different environments. Your doctor can ask questions that would seem much more invasive asked by your mechanic," he added.
They also contend it is not as benign as simply providing consumers with more relevant ads. "Threats to our privacy aren't isolated—they work together," Higgins said. "A tracking device that catches you walking regularly past the door of a store next to a medical clinic may reveal a lot more than intended."
What they'll see
Rebecca Herold, CEO of The Privacy Professor, said that kind of tracking, especially after it is in the hands of third-party firms, "no doubt will be used by many other entities to prove a person was located at a certain place at a certain time, along with what they were looking at. 'Gee, look! Father O'Malley spent 15 minutes reading Hustler magazine right after church! He's a pervert!'" she said is one possible scenario.
"But, you may be implying something that is not the case in real life," she said. "Big Data analytics will be used to reveal a huge amount of perceived activities by individuals, but it will not always be correct."
Presumably, smartphone users could defeat the tracking simply by disabling the Wi-Fi when they are shopping. But Higgins and Herold both contend that the burden should not be on users. "Privacy conscious users shouldn't have to turn off basic features just to avoid excessive tracking," Higgins said.
And Herold said according to some reports, smartphones may be trackable even when they are turned off.
Do Not Track registry proposed
There are some organized efforts being made to give control over tracking back to mobile device users. The FPF and The Wireless Registry are reportedly working to build what would amount to a "Do Not Call" registry for MAC addresses. It would let device owners visit a web site, enter a MAC address, and be assured that tracking companies that have committed to the project will no longer track them.
But it is not certain how soon that will come into being. While the Post reported on October 22 that the site was, "set to launch within the next few weeks," there is little evidence of that. The Wireless Registry website was, as of this week, nothing more than a page with the name of the company on it. Bradish and co-founder Patrick Parodi could not be reached for comment. A public relations spokeswoman said both were attending a conference.

The FPF also did not respond to multiple requests for comment.
And Chris Calabrese, legislative counsel to the American Civil Liberties Union (ACLU), is dubious about the value of such a registry anyway. He notes that joining the project would be voluntary—there will be no law requiring that companies refrain from tracking users who sign up. "The danger is that it leads to more tracking rather than keeping you from being tracked," he said.
Another effort is an agreement announced last month between FPF and seven major location analytics companies—Euclid, iInside, Mexia Interactive, SOLOMO, Radius Networks, Brickstream and Turnstyle Solutions—to a Code of Conduct that will include, "in-store posted signs that alert shoppers that tracking technology is being used, and instructions for how to opt out."
The standards also limit the use and sharing of the data and how long it is kept. It requires the companies to de-identify the data and says it, "cannot be collected or used in an adverse manner for employment, health care or insurance purposes."
The cops will still have access
However, noticeably absent from that list of prohibited uses is law enforcement. So the agreement is small comfort to advocates like Higgins. "When a company starts collecting this data, it becomes a very attractive target for law enforcement," he said.
Herold adds that, "historically, new technologies such as this were viewed as privacy-benign—until something bad happened." She said this is the kind of information that would be very attractive to law enforcement, divorce lawyers and criminals.
"Using the data to improve the retailer environment can be very beneficial. But you cannot ignore all the other possibilities for how that data may be used," she said.
Herold called the Code of Conduct "a good start," but said it is only a start. "We all need to be more aware of ways in which we are giving out our personal data, and limit that significantly," she said, "but we also need to establish information security and privacy standards by which Big Data can be used. There's scarcely anything being done like this now that I'm aware of."
 ROBERT CARDINThe Aegis Portable 3.0 comes in an attractive enclosure with an attached USB 3.0 cable.
ROBERT CARDINThe Aegis Portable 3.0 comes in an attractive enclosure with an attached USB 3.0 cable. 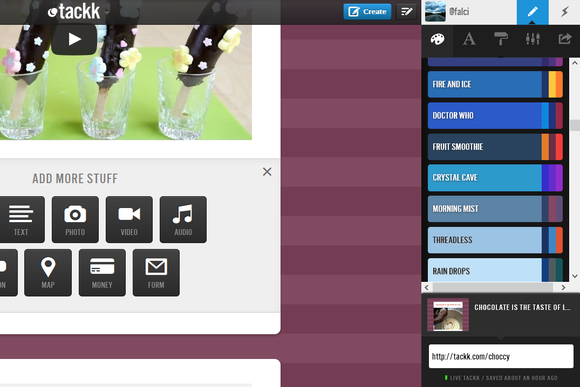 All embed options are in the same place, and include a contact form, a payment widget, and more.
All embed options are in the same place, and include a contact form, a payment widget, and more. 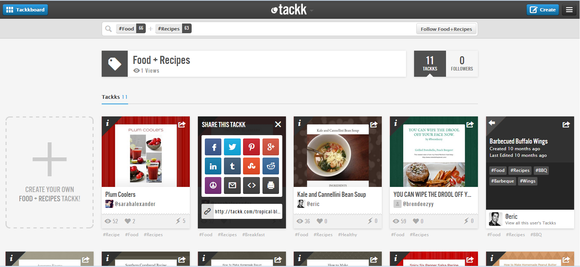 The new Tackk profiles are much more elaborate, helping you promote your personal portfolio of Tackks.
The new Tackk profiles are much more elaborate, helping you promote your personal portfolio of Tackks. 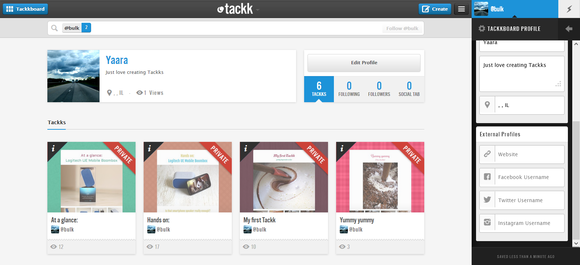 When you search for Tackks, it's easy to find out more about them or share them with one click.
When you search for Tackks, it's easy to find out more about them or share them with one click.  A new social network, Syme, is hoping to attract users with a feel close to Google Plus and Facebook but with encrypted content viewable only to invited members of a group.
A new social network, Syme, is hoping to attract users with a feel close to Google Plus and Facebook but with encrypted content viewable only to invited members of a group.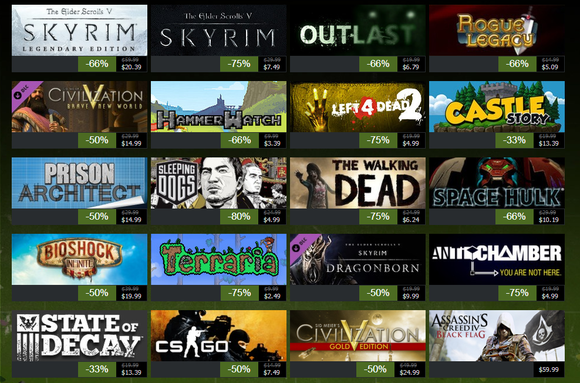 Thursday's cheap games. (Click to enlarge.)
Thursday's cheap games. (Click to enlarge.) TV news anchor Katie Couric is headed to Yahoo.
TV news anchor Katie Couric is headed to Yahoo.




 OnAir, a Swiss in-flight cell carrier, links onboard cellular servers to the ground via satellites.
OnAir, a Swiss in-flight cell carrier, links onboard cellular servers to the ground via satellites.
 Image: U.S. Attorney, Southern District of New YorkWhen he was arrested, Ross William Ulbricht was allegedly logged into a Silk Road account showing a balance of more than 50,000 bit coins. (Click to enlarge.)
Image: U.S. Attorney, Southern District of New YorkWhen he was arrested, Ross William Ulbricht was allegedly logged into a Silk Road account showing a balance of more than 50,000 bit coins. (Click to enlarge.) Image: U.S. Attorney, Southern District of New YorkFederal prosecutors accused Silk Road defendant Ross William Ulbricht of procuring fake IDs.
Image: U.S. Attorney, Southern District of New YorkFederal prosecutors accused Silk Road defendant Ross William Ulbricht of procuring fake IDs. Image: Melissa RiofrioThe half-size cursor and function keys are smaller than we'd like.
Image: Melissa RiofrioThe half-size cursor and function keys are smaller than we'd like.  ROBERT CARDINThe ports include two USB 3.0 and one HDMI for external displays.
ROBERT CARDINThe ports include two USB 3.0 and one HDMI for external displays.